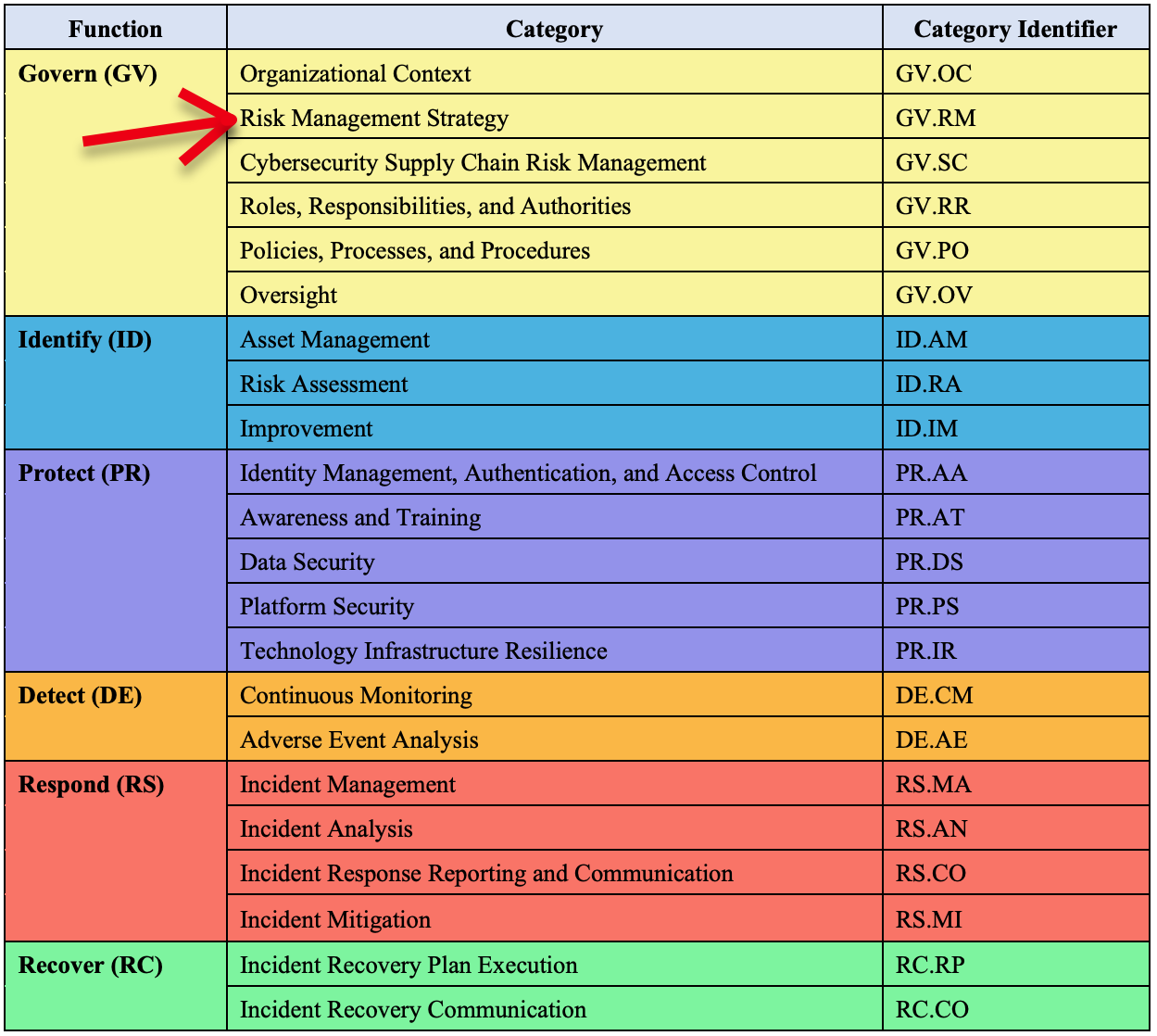
GV.RM-01: Do you know the cybersecurity risk objectives for your organization ?
GV.RM-01: Risk management objectives are established and agreed to by organizational stakeholders. Implementation Examples Example 1: Update near-term …
GV.RM-01: Do you know the cybersecurity risk objectives for your organization ? Read more »